Separation of Concerns
Financial, Reputation, and Regulatory Threats and Weakness
In
2005, a six sigma project was done on the measurements for a county
wide centralized eligibility list. The objective was to consolidate 16
disparate organizations into a single list acquired by all of the
organizations. The primary objective I had in the project was to design
the “to be” state and market research on the potential tools to meet
the contract requirements.
An
in-depth quality assessment was accelerated by the potential to
significantly change the migration strategy. The data was duplicate 80%
of the total volume was reduced to 20% and further refined by
additional quality variables to a fraction of the volume projected for
the county.
The
discrepancies are multifaceted in many cases the zip code and city were
not shown and the agency was in allocation where little to no pockets
of poverty existed. Yet the agencies were acquiring funding based on a
local decision in conflict with the federal sponsors guidance.
Operational/Financial/Management/Quality
Horizontal Flow
The type used to run the business during transactional events used to report revenue or on expenses. In the public sector we refer to this type of data as cost and benefits.
- Record Retention, zero data loss and zero down time are all applicable for the operational scope.
- The best approach for any organization or agency is to separate concerns and DO NOT mix your operational parts of the business with your fit for purpose or analytic decision support systems.
- Choose to mix the two and you have a higher cost on every project.
- You must govern all and assume every release has a potential to influence your key controls.
- Segmenting the operational scope enables speed and agility and a smaller set of applications to invest in P1 support systems.
- Governance around the key control systems has supporting corporate policies and buy-in has greater probability.
Financial Transactions by stakeholder dependency across the life of the activities. Each output becomes the input to the next process stakeholder with a record as an output. The record retention requirements for financial transactions typically is 7 years or more.
 |
| All types shown are record retention for up to 7 years or more, in original format. |
Transaction Capabilities - International and Generic

Today, we are trying very hard to not include these points to avoid this issue with compliance or another which sends up read flags with security.
What's my cure for these types dilemma's? I eliminate or move the threats vectors to their rightful home. Big Data isn't the system of record for financial management capabilities, nor the home for the party or offer management capabilities. For the same reason, a single copy of the expense and revenue transaction capability results are protected within a data store.
How does the suggestion help solve the problems with security, governance and compliance? The 5 capabilities are operational and the foundation of any companies business management system. The scope for Sarbanes Oxley and all regulatory reporting. Record retention requirements with zero data loss and zero down time are all part of the scope.
IF we scale the operational and financial information back to their system of record, integrity of the financial records and retention is not going to hinder the objectives of a big data solution. The technology and requirements are only a problem in regard to the financial and operational processing moving to a big data store.
A great example being records management outside the technology designed to retain records for an organization or agency. The management of data derived from a record is not going to attain the right retention treatment when converted back to a data expert in a data store.
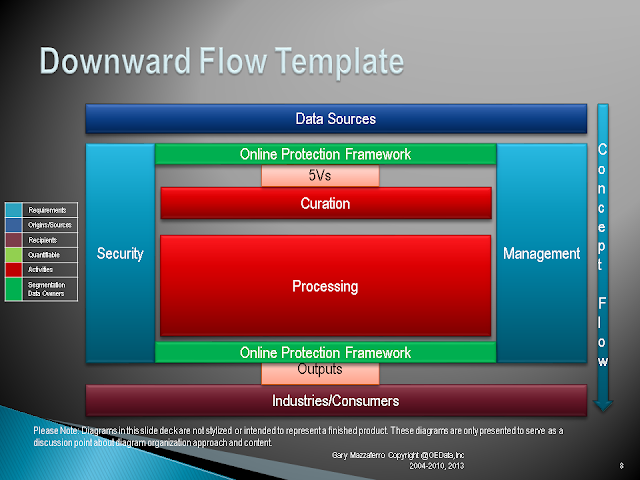
Requirements Capability Template
Gary Mazzaferro supplied this template to the Reference Architecture team in NIST Big Data Work Groups in the first phase of NIST development on the subject.Private Sector
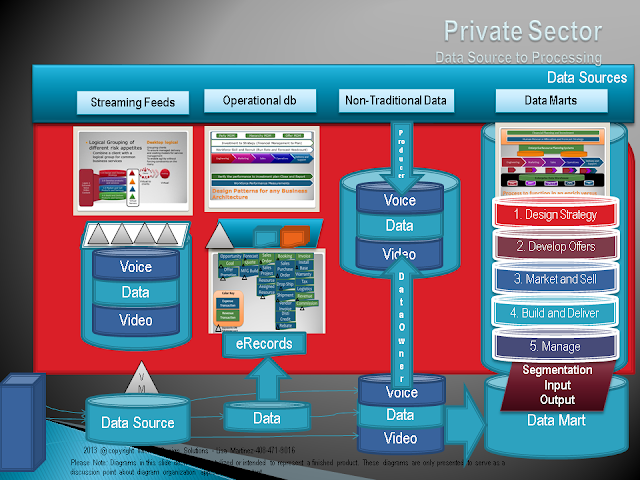 |
| Three types of inbound feeds ensures the proper management of data sources, encryption specifically |
Column 2 Operational (see above)
Column 4 Fit for purpose anything goes information we all know and most peoples desires are in their data marts.
Segmentation
The requirements we hear about are best segmented by the groupings identified as the grouping will manage access and allow containment when sharing beyond the organization in a shared cloud scenario. Marketing allows other marketing stakeholders to access their information.Business Function - Roles based access
We want to avoid situations where marketing grants access to operations data without operations having anything to do with the decision.Public Sector






No comments:
Post a Comment